-
Todas la empresas necesitan documentación, desde las políticas, normas y procedimientos, hasta estándares específicos y guidelines puntuales. Estos activos actualizados mejoran considerablemente los procesos internos dado que ahorra tiempo y mejora la continuidad del negocio.
-
La capacitación es la clave del desempeño de los empleados, cuanto mas capacitado mejores son los procesos. Cursos de seguridad informática, networking, desarrollo seguro, metodologías y sistemas operativos, son algunos de los que disponemos para nuestros clientes.
-
No importa que tan segura sea la red o los sistemas operativos, un error grave en el desarrollo de las aplicaciones generaría una brecha de seguridad desde el centro de los sistemas. La inspección de código seguro que realizamos se basan en los estándares de la industria del software.
-
Los test ASV son análisis de vulnerabilidades obligatorios que realizan las empresas para cumplir con el estándar PCI. A su vez su ejecución brinda una información valiosa sobre las posibles brechas de seguridad de los sistemas, tomando la iniciativa de mitigalo proactivamente.
-
En los últimos años los ataques de phishing aumentaron exponencialmente, ya sea para robar datos de tarjetas, contraseñas o datos bancarios. Este tipo de ataque es facil de realizar, por lo que es altamente recomendable mitigarlo en el sistema de correo electrónico.
-
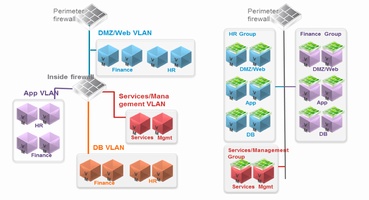
La segmentación de redes en el mejor mecanismo para cumplir con las normas de seguridad internacionales, ya sea PCI, ISO, etc. Es muy significativa la segurar obtenida en la segmentación, por eso que es altamente recomengable realizarla.
-
NESSUS
-
PENTA
-
CISCO
-
MICROSOFT
-
FORTINET
-
QUALYS
ARTÍCULOS
Le recomendamos los siguientes artículos informativos sobre material en ciberseguridad a fin de pueda tener una visión mas clara de la situación actual.
-
CIBERCRÍMENES EN LA ARGENTINA
Los ciberdelitos o delitos informáticos han registrado un aumento sostenido a raíz de la masificación del uso de Internet en las sociedades modernas en general y también en nuestro país en particular. Este incremento puede advertirse tanto en la cantidad de episodios delictivos como en su grado de complejidad y diversidad.
-
SENTIRSE SEGURO ES UNA VULNERABILIDAD
Uno puede decir que al tener una computadora actualizada, antivirus, firewall, sistemas de protección de intrusos y aun así esta inseguro. Nunca se llegará a la seguridad perfecta, es como superar la velocidad de la luz, pero ¿Qué tan lejos estoy de ese límite?.
-
EL ARTE DE AVANZAR O RETIRARSE
La Dip en un concepto empresarial descrito por Seth Goldin, reconocido Gurú de Marketing a nivel mundial. Se fundamenta en diversas situaciónes que todo emprendedor debe afrontar a la hora de iniciar una empresa o negocio y a lo largo de toda su vida. En dicha situación peligra la continuidad de la empresa, ya sea por causas económicas, sociales, legales o personales entre otras. La capacidad de afrontar la Dip es la clave para alcanzar el éxito como empresario.
-
SIEM
Esta implementación se basa en el moniteo activo en tiempo real y reporting de eventos de seguridad, entre otros, de todo el sistema corporativo.
-
IDS/IPS/WAF
Los sistemas IDS/IPS/WEB detectan y frenan los ataques a nivel red y web, tanto interno como externo. Muchas veces require ajustes.
-
CLOUD COMPUTING
El paradigma de Cloud es algo que vino para quedarse, no solo porque optimiza costos, sino que también es rápido y seguro.
-
ENSOBRADOS DE CLAVES
Imagine un sistema que resetea automáticamente la claves, ya sean altamente complejas y con un reporting de uso diario o mensual.
-
BACKUP
Implementar y optimizar un sistema de backup empresarial es crucial para la seguridad y la performance de la red y la continuidad del negocio.
-
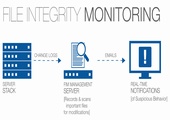
FIM
Muchas normas de seguridad exigen que los sistemas estén integrados a un control de integridad de archivos y una audioría automática./p>
PRESENTACIÓN DE WARP SECURITY
NUNCA SUBESTIMES A UN HACKER
CONCIENTIZACIÓN DE LA NORMA PCI
SLIDER WARP SECURITY
CONTÁCTENOS
En breve nos pondremos en contacto con usted.